The application image file upload allowed authenticated users to upload malious .html files. Opening such a file like https://push.gotify.net/image/ViaxrjzNowdgL-xnEfVV-Ggv5.html would allow the attacker to execute client side scripts. The application image upload will now only allow the upload of files with the following extensions: .gif, .png, .jpg and .jpeg. |
||
|---|---|---|
| .github | ||
| api | ||
| auth | ||
| config | ||
| database | ||
| docker | ||
| docs | ||
| error | ||
| hack/packr | ||
| mode | ||
| model | ||
| plugin | ||
| router | ||
| runner | ||
| test | ||
| ui | ||
| .editorconfig | ||
| .gitignore | ||
| .golangci.yml | ||
| CODEOWNERS | ||
| CODE_OF_CONDUCT.md | ||
| CONTRIBUTING.md | ||
| GO_VERSION | ||
| LICENSE | ||
| Makefile | ||
| README.md | ||
| SECURITY.md | ||
| app.go | ||
| config.example.yml | ||
| go.mod | ||
| go.sum | ||
| ui.png | ||
README.md
gotify/server
Intro
We wanted a simple server for sending and receiving messages (in real time per WebSocket). For this, not many open source projects existed and most of the existing ones were abandoned. Also, a requirement was that it can be self-hosted. We know there are many free and commercial push services out there.
Features
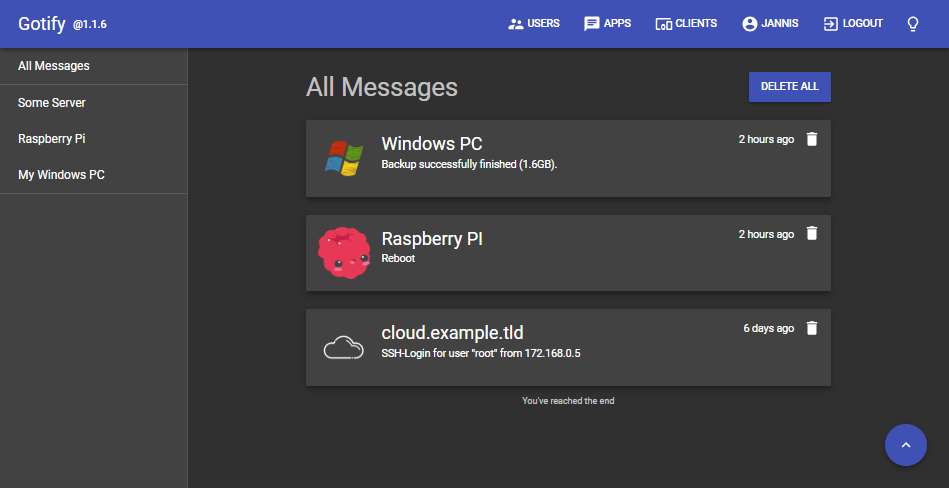
- send messages via REST-API
- receive messages via WebSocket
- manage users, clients and applications
- Plugins
- Web-UI -> ./ui
- CLI for sending messages -> gotify/cli
- Android-App -> gotify/android
(Google Play and the Google Play logo are trademarks of Google LLC.)
Install ᛫ Configuration ᛫ REST-API ᛫ Setup Dev Environment
Contributing
We welcome all kinds of contribution, including bug reports, feature requests, documentation improvements, UI refinements, etc. Check out CONTRIBUTING.md for guidelines.
Versioning
We use SemVer for versioning. For the versions available, see the tags on this repository.
License
This project is licensed under the MIT License - see the LICENSE file for details